Machine Mayhem
For every human identity, there are at least 80 non-human identities. Traditional IAM just can't keep up.

Learn more
80:1. That's the ratio of non-human to human identities. Your service
accounts, keys, and tokens dominate your attack surface


NHIs are growing, and introducing vulnerabilities with them. Your tokens, keys, and service accounts are gateways to your environment - and can be exploited by outsiders to gain production access.
For every human identity, there are at least 80 non-human identities. Traditional IAM just can't keep up.
You can't secure what you can't see. Most organizations lack a true NHI inventory.
NHIs are quickly created, rarely managed, and often outlive their purpose.
NHIs are often granted more access than they need. It's an easily preventable breach waiting to occur.
With unsecured and unmanaged NHIs, your enterprise secrets are sitting ducks for breaches.
NHIs lack human-like governance with no onboarding, rotation, revocation, or regular review.






Google workspace
Entra ID
Teams
Active directory
Okta
AWS
Docker
Circle CI
snowflake
GCS
Secure your entire modern environment
from code to cloud.
Azure Blob
Git Hub
Air Table
ECR
GitLab
Azure Repo
Google Chat
One Drive
S3
slack
Hugging face
Bitbucket
OCI
Postman
Jenkins
Webex
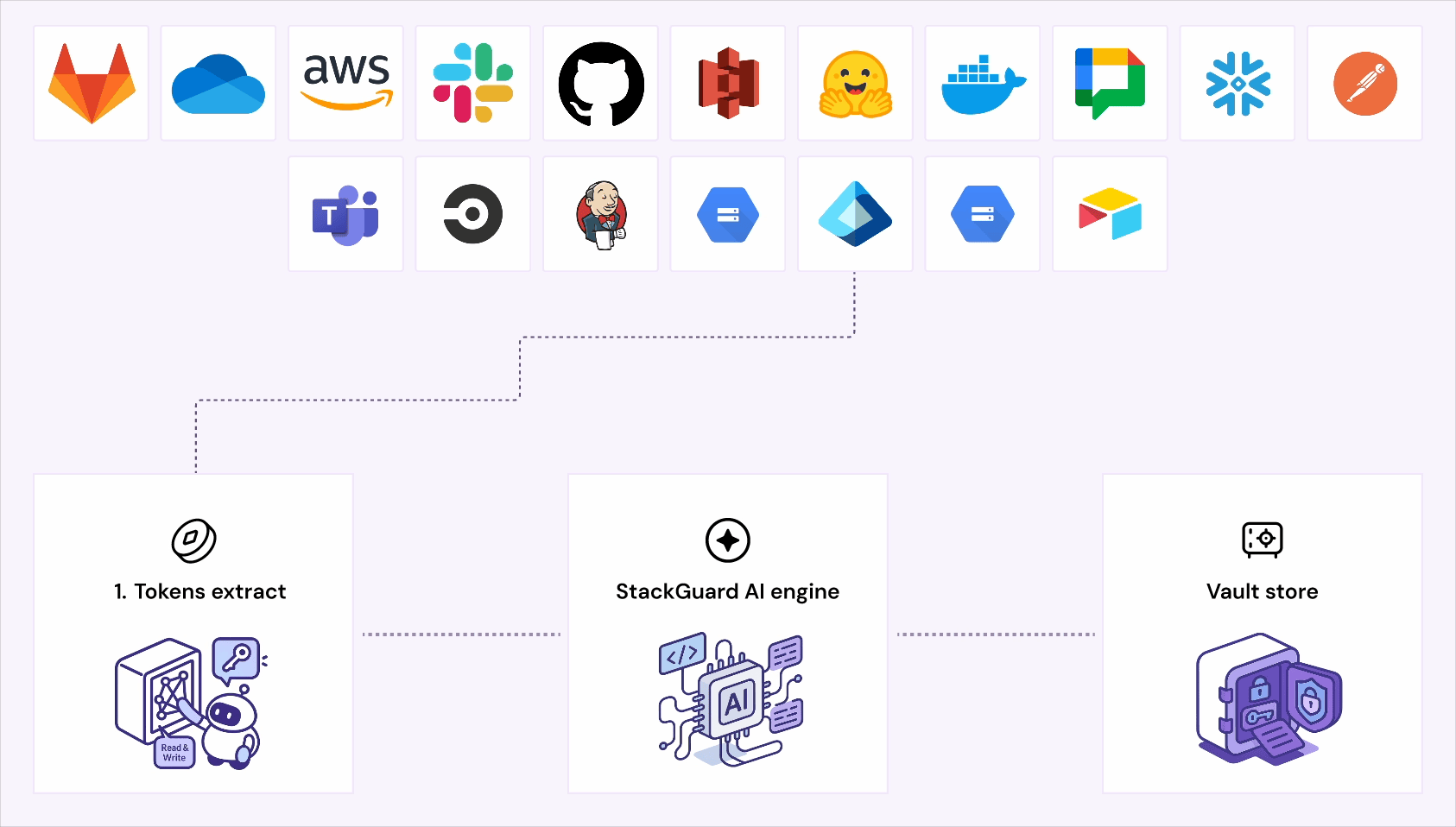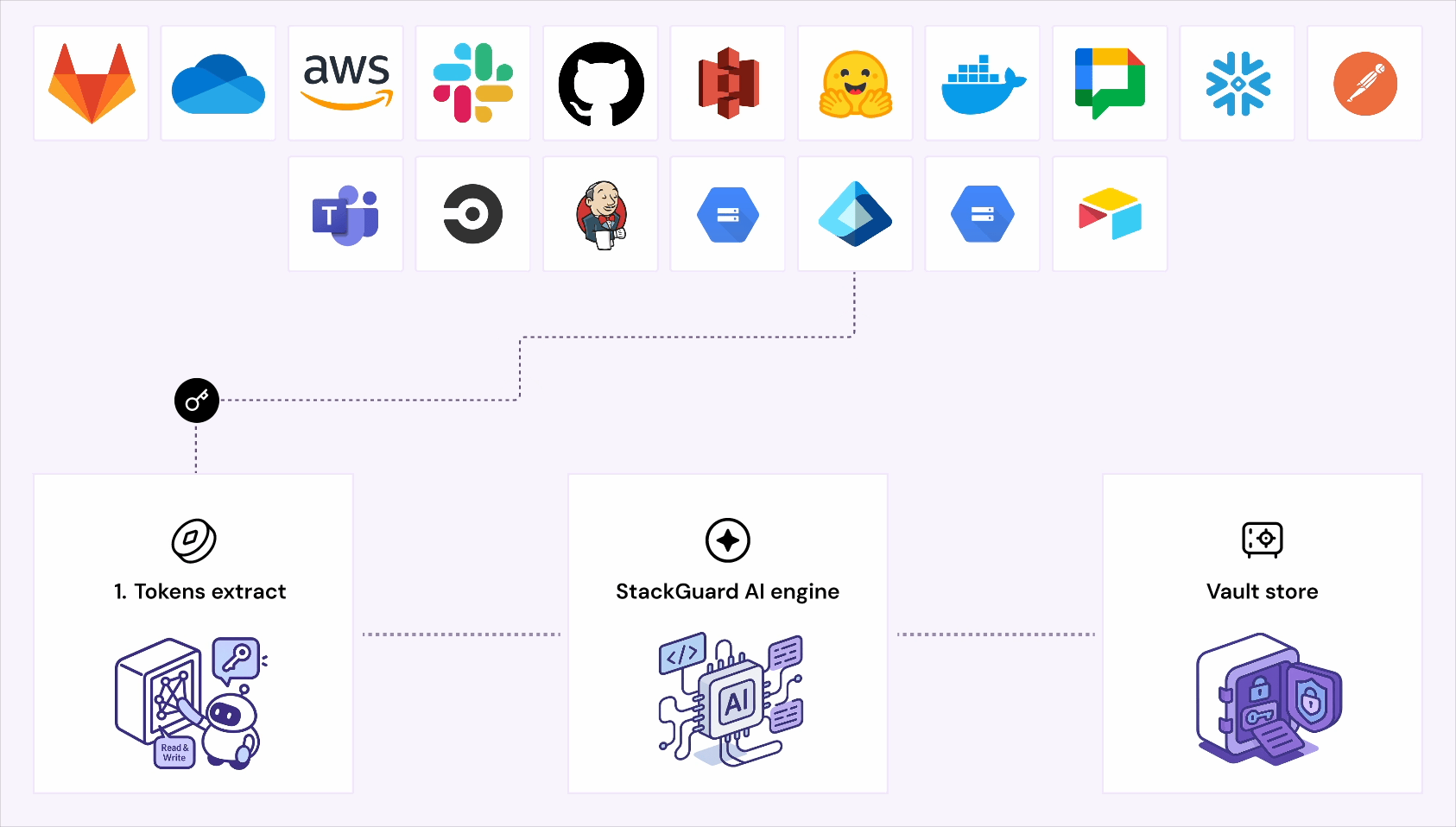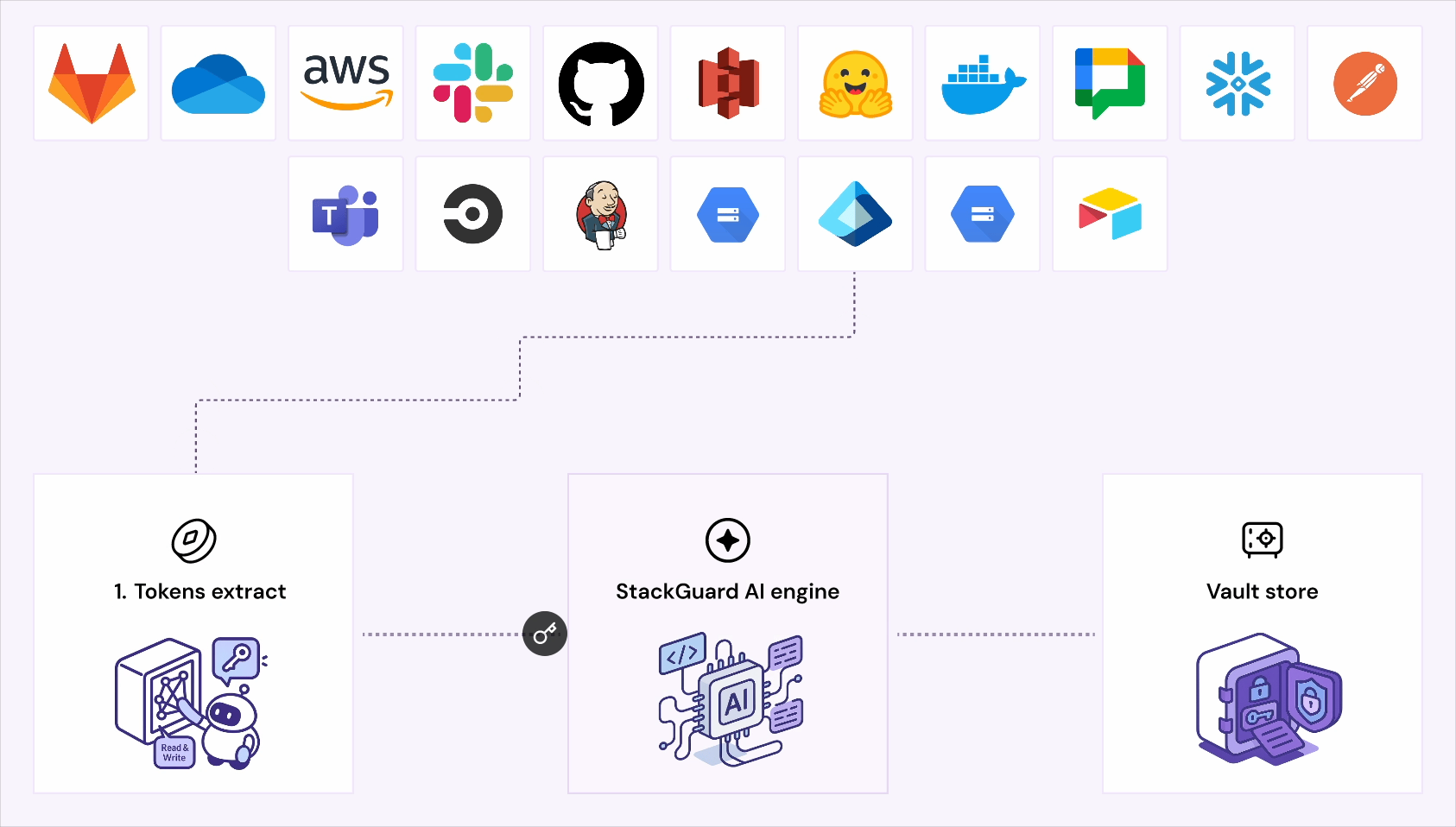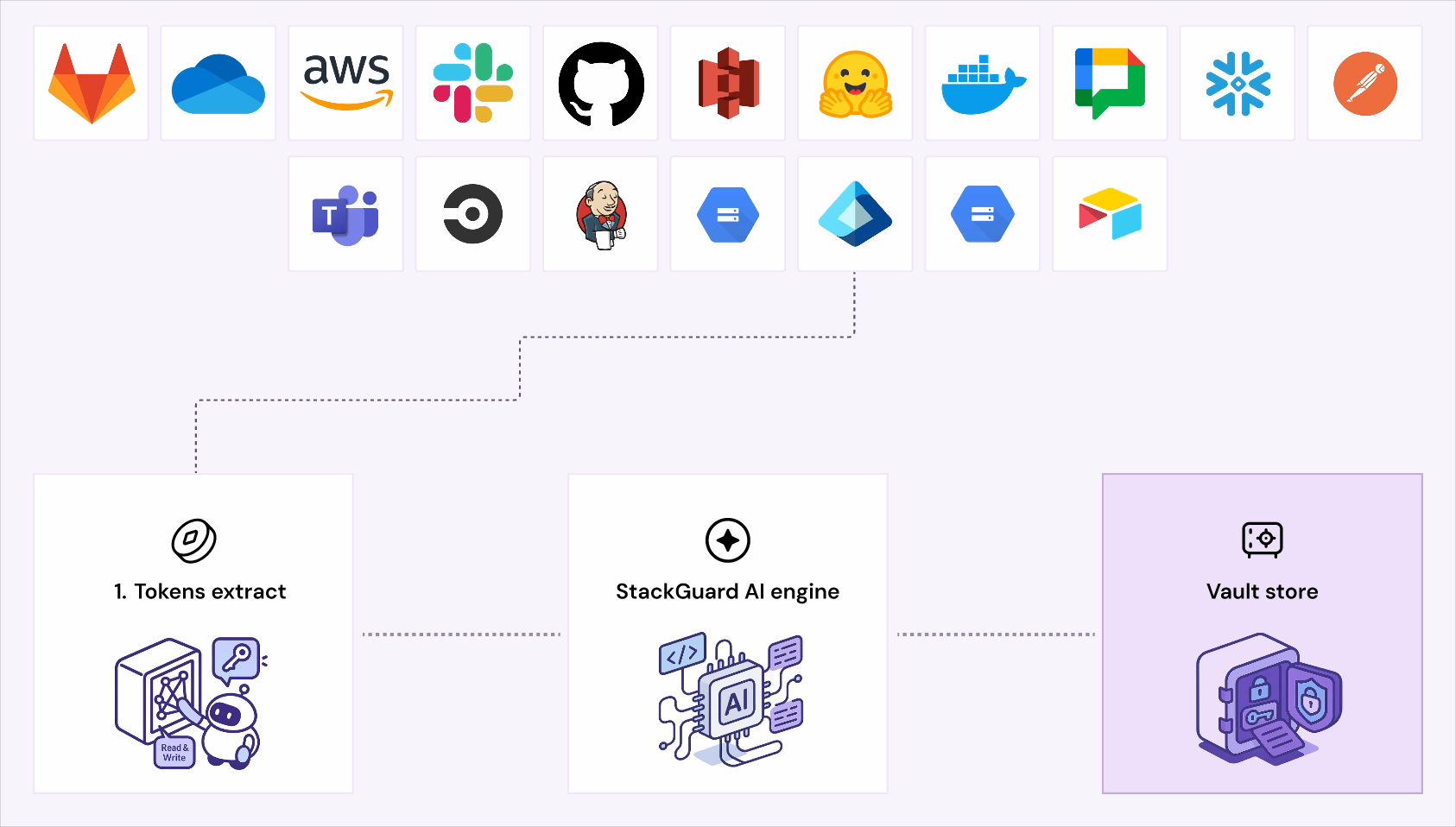
Unseen tokens. Shadow identities. Silent exposures.
Most breaches start silent and unnoticed.
StackGuard uncovers every NHI and shuts down risk
before it spreads.